Ransomware
Ransomware intentionally encrypts important files on your computer and causes great damage. Learn how you can protect yourself against digital blackmail with TeamDrive.
What is Ransomware?
Ransomware is derived from the English word “ransom”, which stands for ransom in German. The second part of the word “ware” implies that ransomware is software. Ransomware is a program that can attack the hardware of an IT system. This includes components such as servers or computers as well as mobile devices such as tablets and smartphones. Ransomware also does not spare certain operating systems. Therefore, Windows, Linux, Android or macOS are potentially at risk.
Synonyms for the term ransomware are encryption trojans, blackmail trojans or crypto trojans. They are considered as malware. The Trojan manipulates the computer of victims and then extorts money. The malware only holds out the prospect of reversing the harmful change to the IT system once the victims have made a payment. However, paying a ransom is no guarantee that the malware will actually decrypt the data again. It can happen that files are lost forever in the event of a ransomware attack.
The danger posed by malware already has a long history. The first major threats from Trojans were caused by the distribution via a floppy disk. The first ransomware AIDS Trojan Disk infected the first computers at the end of the 1980s, when there was no Internet. From 2005 onwards, users of social networks increasingly became victims of ransomware. Ransomware attacks on Windows systems have also increased.
How does ransomware get onto an end device?
An encryption Trojan gets onto an end device like a virus. A ransomware attack is often carried out via phishing e-mails with attachments or dubious links. Anyone who opens such e-mail attachments or clicks on a link gets harmful ransomware or malware into their home. The attachment of an electronic message usually contains ZIP files. They feign important content to users. These include an invoice, reminder or confirmation for supposedly ordered items. Ransomware attacks via e-mail use the principle of social engineering. They play with people’s fear and try to elicit a certain behavior.
Very often we also find in the mailbox alleged mails from official authorities or companies. They are particularly deceptive, because their depiction makes them appear to be strongly authentic. In these cases, users are supposed to check their bank account or report to the police for criminal offenses, for example. Even fake e-mails from the Federal Criminal Police Office, providers or software companies lure gullible users into the ransomware trap.
Another gateway for such malware is security holes in browsers we use to surf the Internet. Widespread cloud services such as Dropbox or Google Drive also offer a passage for ransomware attacks. In recent years, harmful advertisements, so-called adware, have appeared rather rarely. They entice users to click on otherwise reputable websites. As dangerously coding Trojaners act, we look now somewhat more exactly at ourselves.
Source: zdnet.de
What damage does ransomware cause?
Ransomware encrypts private or sensitive files that are located on a hard disk. At first the user has no access to this information. The malware also blocks easy access to the computer.
A window with hints usually appears on the screen. Anyone who does not know how to deal with this will pay a ransom to the blackmailers desperately and hastily. They often demand cryptic currencies like Bitcoins or prepaid cards as means of payment.
Much more dangerous is an infestation with ransomware, which encrypts important data. This can affect entire databases, folders with photos or documents. Well-known and frequently used file formats such as Microsoft Office documents are particularly at risk. An affected user can only access these files with a password. However, he or she only gets this through a payment. This clearly shows the difference to spyware. The files remain on the IT system, but are no longer accessible. Spyware is known to move considerable amounts of data to third parties or offer advertising product ads.
What to do in case of a ransomware attack?
If you do not protect your IT system sufficiently, you are not safe from a common encryption Trojan. But what to do if a cyber attack is carried out with ransomware? Paying money to criminals is out of the question under any circumstances. Extreme caution must be exercised in the event of an attack with an encryption Trojan. Malware continues to infect an end device when the user uses other programs. The input of passwords is particularly critical. Definitely refrain from instructing a payment via online banking. Keep the damage caused by Ransom attacks as low as possible. Anything else would be considered gross negligence.
The first step after a cyber attack by a blackmailing Trojan is to switch off the terminal device. The recommendation here is not to switch off the device as usual, but to disconnect it from the power supply or battery. This does not block unencrypted content. We advise against paying a ransom to the blackmailers. There is no guarantee that encrypted files will be decrypted afterwards.
This is what the perfect ransomware protection looks like
Almost daily, millions of computers are threatened by ransomware, viruses or Trojans. They unintentionally encrypt data. Companies, but also private users, have various possibilities to protect themselves from these harmful programs. The protection of data is one of the most important tasks, both for private users and for companies. If you do not think about ransomware and ransomware protection, you risk losing important data and a lot of money.
Careful protection against ransomware prevents bad and expensive surprises. With TeamDrive and just a few clicks, users can continue working as if nothing had happened in the event of a ransomware attack. Attacks by ransomware can be avoided by the following measures:
TeamDrive protects data from an encryption Trojan
Despite all precautions to increase IT security, an infestation with ransomware, malware or viruses can never be ruled out. Those who create backups usually store data on an external hard disk. If this is connected to a device that has been infected by ransomware, the stored data looks bad. There is also a second weakness when backing up data on external hard drives. Users often do not perform regular backups.
For comprehensive ransomware protection, TeamDrive offers comprehensive and automated data backup in the cloud. We encrypt the content to protect it from unauthorized access. Thanks to backup, the data is well protected and available in an up-to-date form. The reason for this is the automated, continuous synchronization of data to prevent data loss. We call this Point in Time Recovery.
Data synchronization from the cloud after a system crash
Occasionally, users who become victims of ransomware have to completely reinstall their system. Anyone who regularly creates backups with a cloud service such as TeamDrive can then transfer all data back to the end device. If, instead, there is only a backup on a USB stick, the loss of data is likely. The advantage of synchronized files in a cloud is that users always have the chance to retrieve the last automatically backed up data.
“Storing data on your own PC or server is potentially more dangerous than backing up data in our cloud service,” explains Detlef Schmuck, Managing Director of TeamDrive. For this reason, it is advisable to back up all important data beyond your own IT infrastructure in the cloud. Full end-to-end encryption also ensures that only the owners of the security key read and process the data.
List of known ransomware variants
In recent years, several different ransomware programs have already caused great damage. The following list shows selected ransomware variants:
More blog posts about ransomware:
Further knowledge from the topic of ransomware
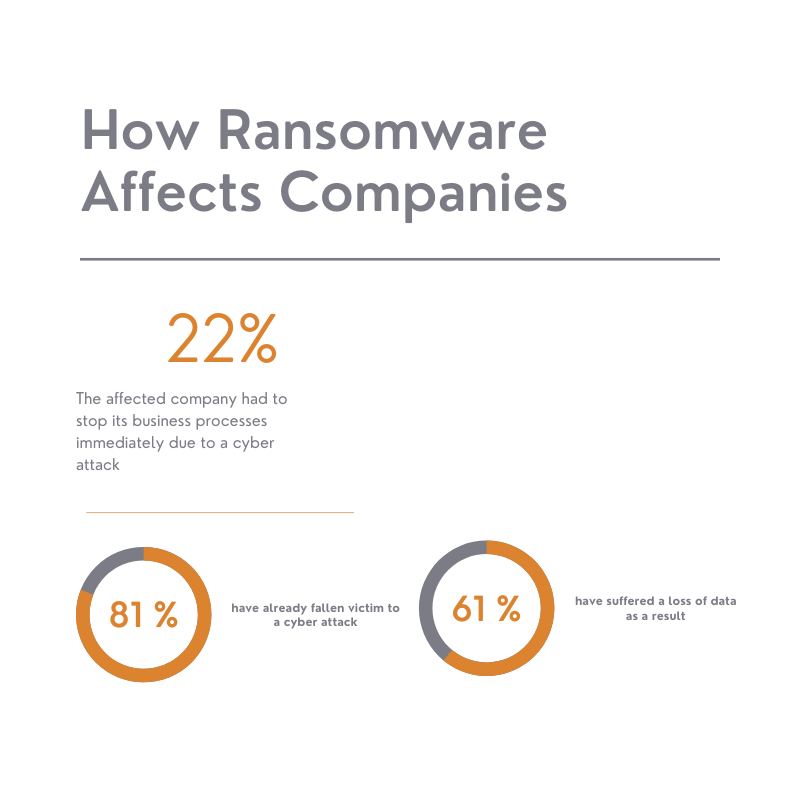
Ransomware attacks have increased significantly in recent years. After a successful attack, all data on your computer is encrypted. From this moment on you no longer have any access options. The economic damage to companies is often enormous.
Find out here how you can protect yourself against digital blackmail.
Further knowledge in the areas of data transfer and data storage
In the beginning, cloud computing was primarily understood to mean the provision of storage volumes via central data centers. Instead of buying storage, you could rent storage flexibly and as needed.
This continues to happen today in varying degrees, but the offering has been expanded to include numerous other interesting services from cloud providers.
A backup is a backup copy of data that can be used to restore data if the original data is damaged, deleted or encrypted.
In the best case scenario, a backup should be stored in a different location than the original data itself - ideally in a cloud. You can find out why this is the case and what this has to do with ransomware attacks here.
With the introduction of the General Data Protection Regulation, DSGVO for short, extended requirements came into effect, especially with regard to personal data protection - including sensitive sanctions for violations of the law.
Read here what effects the GDPR has on you and your company.
The ePrivacy Regulation, which is still a work in progress at the moment, will also be discussed, but will in future formulate binding data protection rules that will apply within the EU.
According to the Principles of Proper Accounting (GoBD), data and documents that are to be recognized by the tax authorities for tax evidence must be handled in a special way.
We will explain to you the most important facts about archiving and storing electronic documents.
In the digital age, data protection and data security play an outstanding role.
To ensure that electronic data cannot be viewed by third parties and to prevent data misuse, it must be encrypted. This applies both to their storage and, above all, to their transport via the public Internet.
You can get deeper insights into the topic of encryption here.
Especially with software that is intended to protect your users' data from unauthorized access by third parties, software and data security must be taken into account and integrated into the entire software life cycle.
You can find out why this is very important and how you as a user benefit from it here.
